SOAR (IAM-PAM-AA)
About IAM-PAM-AA
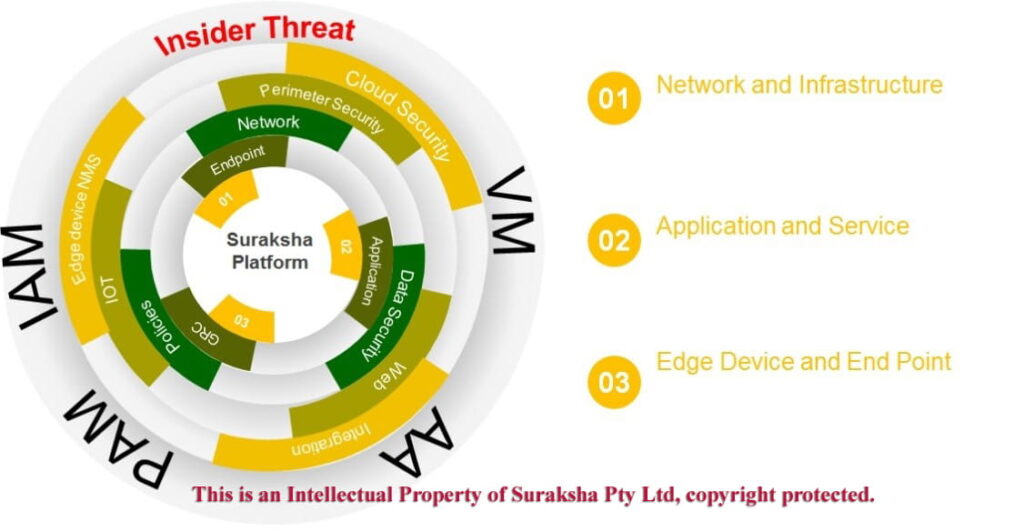
Cyber criminals are combative and tenacious in their attempts to compromise networks, data, financial transactions, infrastructure and manipulate user behavior. They continuously develop new tactics and methods to overcome defense mechanisms in place and misuse state-of-art technologies. Their attacks concentrate on the most vulnerable link of the architecture and the outcomes are disastrous. The issues in this domain can be grouped into three main categories, described briefly below:
- IAM (Identity and Access Management) – The rapid spread of mobile, social and cloud platforms have reduced the effectiveness of traditional firewalls. Digital signatures have become critical for monitoring access to information. Hence, IAM has become a hot topic in boardrooms across the world as various breaches have happened because of failure to efficiently administer user access.
- PAM (Privilege Access Management) – Privilege accounts are the most powerful in the organization. They are high value targets for cyber criminals who try to get access to customer data, resources and confidential information. Due to an increase in breaches and insider threats, PAM has become a top priority.
- AA (Access and Authentication Management) – Access and authentication management is vital in present world where identity theft and unauthorized access is rampant. It has become necessary to have more than one facet of authentication process and contextualise access request.
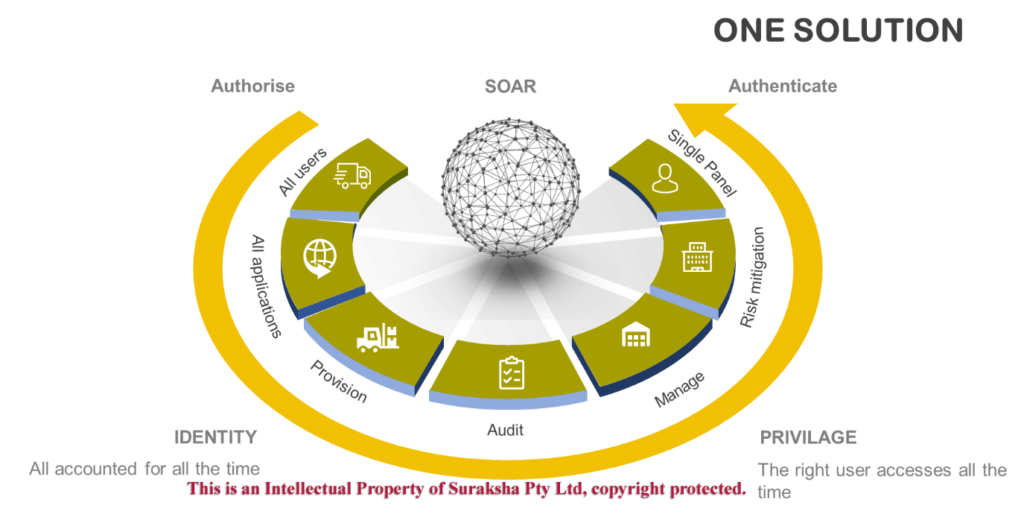
Suraksha’s Solution: Suraksha Orchestration and Response (SOAR)
The Suraksha’s SOAR platform integrates several top-notch products, which are the global leaders providing competitive security solutions. The key distinguisher is, all these products are well integrated and operate with common source of data.
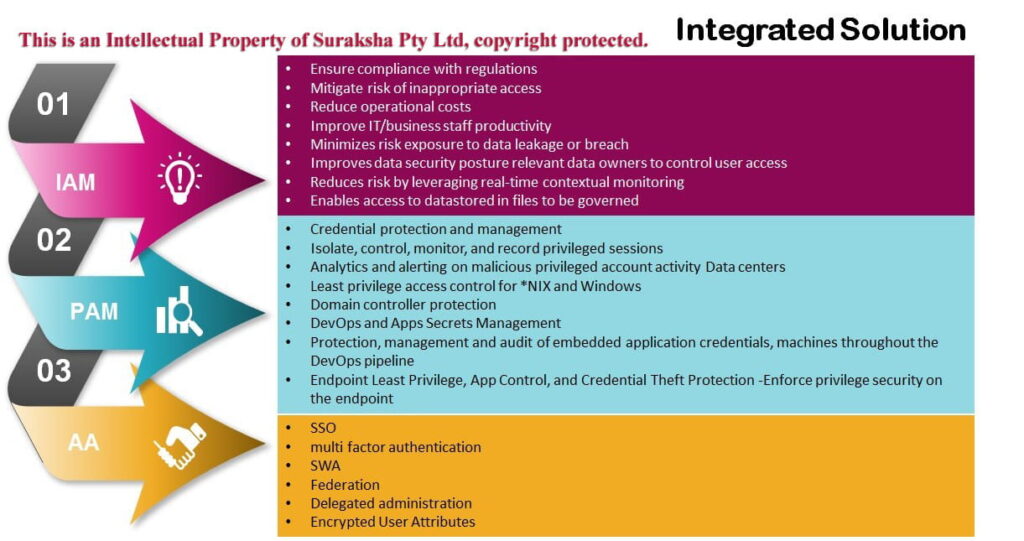
- IAM product suite, which includes Compliance Manager, Lifecycle Manager, Governance Platform and integration modules
- Complete IAM solution including OS, apps, cloud, databases and most IT environments.
- Granular Privileged Access Controls (PAM)
- Protection of all privileged account passwords and SSH keys in a highly-secure central repository to prevent the loss, theft or unauthorized sharing of these credentials
- Simplified management of privilege through comprehensive automation controls
- Centralized Secure Storage
- Role Management – Detect, Mine and Model Roles
- Detailed Audit Reporting and audit trial for Compliance
- Automatic Credential Rotation
- Re-Encrypt passwords using different Encryption Keys
- End-to-End Automation
- Identify, Baseline and Score, Application and Identity Risk
- Policy Management – Define/Update Policies and Rules for Risks/Accounts/Duties/Activities
- Universal Directory – A flexible, cloud-based user store to customize, organize, and manage any set of user attributes
- Single Sign-On – A single set of credentials giving access to enterprise apps in the cloud, on-prem, and on mobile devices
- Lifecycle Management – Automated user onboarding and off boarding with seamless communication between directories and cloud applications
- MFA – Secure apps and VPN with a robust policy framework, a comprehensive set of modern second-verification factors, and adaptive, risk-based authentication that integrates with all of apps and infrastructure
- Secure Personnel Practices, Platforms and Customer data
- Create your own crypt to give direct asset access to authorized users with lock/unlock features
- Add Safe-deposit box to the crypt. Rename/Modify the password/any property any time, as well as this can be deleted when no longer needed
- Set-up and Manage Service Accounts and Object Level Access Control
- Custom Reports using the data retrieved with extended validation and display
- XML Representation of Reports and Instances
- Design and Set up Workflows with custom tasks/process and subsequently monitor them using several libraries
- Notification features by configure custom Email templates for various events
Suraksha’s Solution Approach, Services and Benefits
| Audit and Assurance | Solution |
|---|---|
| Platform Evaluation Solution Assurance Standards and Conformance Legislation and Compliance Risk Assessments | Product deployment Platform based services Solution and Managed services |
Security Audits – One of the key factors that usually gets missed but emphasized by Suraksha is assessing the current security posture of the devices through a security audit. This is vital to identify and measure the gaps and vulnerabilities. So that they could be targeted specifically to uplift your organization’s security standards beyond the benchmark and make your operations risk free.
Trust in Experience – Suraksha is equipped with auditors who are having 30+ years of expertise in the domain and conduct audits against international standards. This ensures your company’s security standards are competitive and world-class.
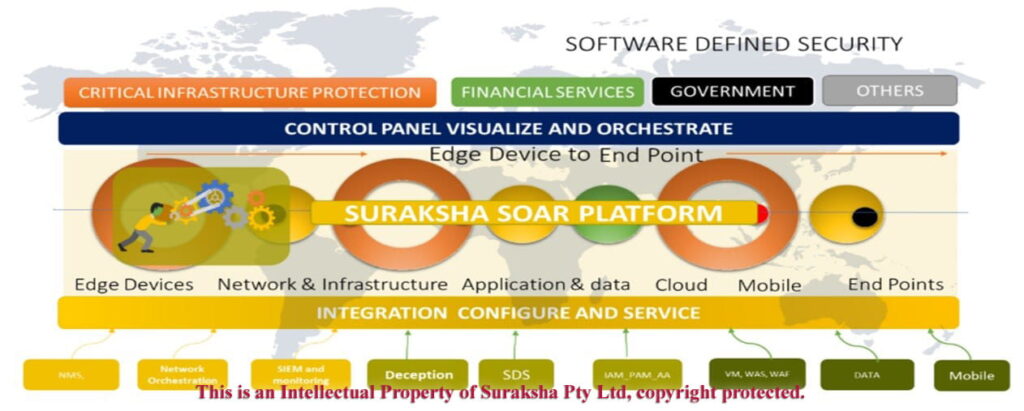
Central management of security – Implement, control and manage threats from one single place by integrating several products (Click here to see the Suraksha Software Defined Security). Suraksha has partnered with the industries best and you could enjoy the privileges from several products in one place. A, “One Stop Shop”.
With an Industry expert and specialists, offering 24/7 support, there is no better place to start securing your assets. Proactively protect against, detect and respond to in-progress cyber-attacks before they strike vital systems and compromise sensitive data. Take a simple step of choosing Suraksha and Enjoy peace of mind!
About Suraksha
Suraksha is an Australia based Information Security company, with Suraksha Information Security Qatar, operating in Qatar expanding its operations into Asia, Middle East and USA rapidly. The vision of Suraksha is to provide a safe and secure, business and home environments by using technology as an enabler. The mission is to provide solutions, processes, technology and personnel for information security to ensure a reliable, robust and consistent business environment.Click here to see Suraksha contact details

