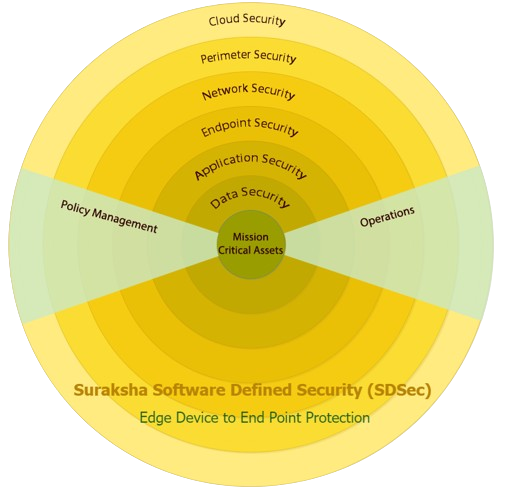
Suraksha Products & Services

Edge Device Protection
When it comes to protecting the Internet edge, you need to see the users, applications, devices, and threats on your network and what they are doing. With next-generation security services, ASA 5500-X firewalls protect your business, regardless of size, against multivector threats across the entire attack continuum.
Your business can take advantage of new applications and devices — balancing security effectiveness with productivity — using ASA 5500-X Series Next-Generation Firewalls (NGFWs). This solution offers the combination of the industry’s most deployed stateful firewall, with a comprehensive range of next-generation network security services.
Network Protection
In order to assist Clients in achieving its objectives, Suraksha Network Solution proposes an approach with the following set of activities:
- Vulnerability Assessment – Performing Vulnerability Assessment
- Web Application Security Assessment – For Web Applications in scope
- Penetration Testing – Performing Penetration Testing
- Web Pages
- Web Applications
- Applications
- Server Infrastructure
- Network
- Mobile Devices
Suraksha proposes the following methodology to be followed for meeting Queensland Government’s objectives in a manner that best suites the existing security environment with maximum benefits
Suraksha’s Network security services are:
- Rapid detection of advanced threats enabled by big data analytics technologies
- Exceptional technology accountability with control management and security event monitoring
- Effective resource allocation with a high-fidelity focus on advanced threat detection and triage
Managed Security Services combine a breadth of security technologies, intelligence, analytics, and a team of world-class experts that only Suraksha can provide. This gives customers complete control and visibility of the entire security event lifecycle.

End Point Protection
Endpoint Security infuses high-fidelity machine learning into a blend of threat protection techniques, eliminating security gaps, and providing maximum protection for today’s and tomorrow’s threats across endpoints and users.
Security should not slow you down. It optimizes performance by using the right technique at the right time. Plus, you’ll spend less time on administration with centralized visibility and control.
SIEM
Information event management from Suraksha offers around-the-clock security monitoring and reporting to help you improve your security and compliance posture and better protect critical data.
As network traffic and complexity increases, threat and compliance issues call for real-time alerting, correlation, analysis and auditing that can only be accomplished with security information and event management (SIEM) technology and a vigilant team of IT experts. Suraksha Managed SIEM services provide world-class expertise, threat intelligence, efficiency and automation otherwise unavailable to most organizations.
We at suraksha help protect your enterprise with better security intelligence and expertise.
Data Protection
- Data security strategy and assessment
- Data loss protection
- Enterprise wide data and content protection services

Services could include:
- Video surveillance, systems including still and moving image
- Configuration change tracking, management and validation
- Physical access control, authentication and monitoring, including card key or biometrics scanning systems
- Locked or secured access cabinetry for servers, storage and networking gear as well as secured access to cabling and patch panels
- Secure disposal and disposition of retired IT equipment and media
- Asset and media tracking, including implementation of RFID-enabled tape volume labels, RFID scanning of tapes and removable disk drives (RDD) and GPS-enabled tape case tracking
Operational Technology Protection
Over the last several decades, as industries transitioned from analog and pneumatic controls to digitalized PLCs, DCS and SCADA systems, Operational Technologies (OT) have provided plant personnel with ever increasing volumes of data to monitor, optimize and control industrial processes; however, there has not been a clear path for organization to leverage this data outside of OT domains. Differences in IT and OT functions, technology stacks and cultures have created significant barriers to OT-IT convergence.
An enterprise initiative to develop and utilize a common technical infrastructure that aligns Operational data (OT) with business data (IT). OT-IT convergence harmonizes operational and business data, enabling leadership teams to calculate enterprise KPIs and track how asset performance, process efficiency and quality affect revenue.
Services:
- AS-IS analysis design and architectural review
- Snap audits of cyber risks
- Threat and Risk Assessments
- Internal audits for compliance obligations
- Risk mitigation services
- Cyber assurance services (3rd party independent vendor assurance)
LTE & Telecommunication Protection
With the increased use of sensitive electronics in telecommunications, signal and data management, effective surge clamping is essential to prevent data corruption, component damage operational downtime, loss of revenue, customer dissatisfaction and risk to human safety.
Suraksha is an acknowledged leader when it comes to delivering telecommunications security solutions to telecommunications companies operating at the local, regional or national level. We provide seamless protection for communications, switching and routing equipment, transmission facilities and towers. We will also protect employees and property at your call centers and retail stores, along with the critical backbone components of your network.