Suraksha Software Defined Security
Optimise Your Cost and Reduce Risk with SSDSec Services
A “One stop shop” for security across the architecture from Edge Device to End Point software-defined security (SSDSEC) to virtually disconnect your network from everything but trusted resources.
Edge Device to End Point Protection
The Suraksha Software-Defined security platform provides security for organizations across geographic boundaries and on an architecture that is Vendor Agnostic.
As a service provider, one will be able to visualize, control, manage and orchestrate security functions with minimal business disruption.
Defence in Depth
Security Platform (SSDSec) is a software-based Network Security solution that delivers adaptive security and connectivity for data centres and clouds. Security Platform CLOAKS applications and resources and enables impenetrable secure private communications across all application workloads whilst creating “a true isolation and total containment for each application environment”.
Security Platform is architected around three key components: SSDSec Engine, Agent, and Analytics.
The SSDSec is a web-based management system that is used to monitor, configure, provision, and manage all the SSDSec Zones. The Security Platform uses SSDSecZones to:
- Create secure, isolated overlay networks that can contain resources distributed across different geo-locations, data centers and clouds.
- SSDSecZones enable encrypted and cloaked communication paths between resources. agent installed on the resources enforce policies, report health and network activities, and provide encryption and decryption services.

Manage security with minimal business disruption
With SSDSec, you can create Business Applications that:
- Logically group resources hosting the components on an application
- Secure your Applications against attacks – by assigning Security Policy Templates and Connection Information that contain rules to allow or block connections between resources.
Analytics is a component that is integrated with SSDSec Engine to capture and store statistics for communication between resources and provide reports that you can view in SSDSec Engine.
SSDSec offers the following benefits:
- Instantly connects all application end-points and services from anywhere – data centres or clouds – without any change to existing infrastructure elements like routers, switches, firewall and other infrastructure.
- Offers always-on point-to-point encryption.
- Keeps application and data completely non-reachable and isolated from any unauthorized access.
- Establishes a digital identity and access for applications, users, resources, or any other components.
Thus a Consolidated Security Platform provides a paradigm shift in enterprise IT security as it makes the offering platform independent, enables security product consolidation and reduced operational complexity
How to Reduce Gaps in Security and Create Cost Savings?
“Secure Micro-Segmentation” is used to automate security tasks by segmenting and hiding resources and defining logical zones of trust that adapt automatically even if the resources move into other zones
- “Trust Policy Orchestration” helps to manage – app, workload, users, and infrastructure actions across hybrid environments from a single pane of glass.
- “Identity-Based Networking” to leverage cryptographic techniques to ensure users and devices access to workloads are protected above and beyond just basic identity access management.
- “Intuitive Risk Analytics” that identify threats and their impact vectors at the workload, business application, cloud, segment or even corporate-wide infrastructure levels.
Consolidated Intent Based Enforcement (Intent Enforcement)
Intent Enforcement creates a zero-trust environment by enforcing resource actions and collecting telemetry information to help not only stop policy violations but also to determine malicious resource intent. With Policy Modelling and Policy Based War Gaming, organizations can visualize “what-if” scenarios for accurate policy deployment or even probing the resiliency of the organizations.
- Secure, platform-independent micro-segmentation
- Zero-trust network with full visibility, analytics and control
- Proactive threat protection from zero-day, APT and other emerging threats
- User and application end-point security without additional/expensive chokepoints (firewalls)
- Reduced operational overhead – No ACLs and thousands of firewall rules
- Reusable security policy templates for security automation
- Intuitive application risk posture analytics for quick remediation
Consolidated Secure User Segmentation and User Access (Secure User)
Secure User securely enables users to access only those apps they are authorized to access. This goes beyond simple identity and access management and looks at the risk level the user provides to the workload. By combining the user risk and ensuring the user has only access to the specific apps required, insider theft or compromised resources/ credentials no longer pose a threat to the workloads.
- Rapid, platform-independent environment separation
- Zero-trust architecture with continuous cross-segment traffic visibility
- Privacy, compliance and security assurance
- Reduced attack surface
Consolidated Deception Enforcement (Cloaking)
Cloaking reduces the attack surface by hiding critical resources. This approach simplifies the execution of zero trust networking by proactively eliminating the potential target.
Outcomes:
- Lowered Attack Volume: Fewer attack surfaces/objects visible for probing results in lesser attacks. Zero-trust model reduces internal threats as resource exposure is permitted only during a transaction.
- Reduced Operational Burden: Lowered attack volume reduces operational overheads. Instead of reviewing thousands of logs, the security and IT teams can focus on more sophisticated threats that require human intervention.
- Easier Hybrid Cloud Management: Cloaking is built on an architecture that allows for security policy to follow the workload. This means, in practice, the workloads can move from on-premise data center to cloud data center and security policies follow the work load independent of the underlay infrastructure.
- Mitigation of Lateral APTs: As a corollary to the above points, should an infection enter the data center, the malware or hacker cannot progress further beyond the trust relationship provided to the resource. This is a more effective way of protecting data centers from APTs when compared with traditional ATP vendors.
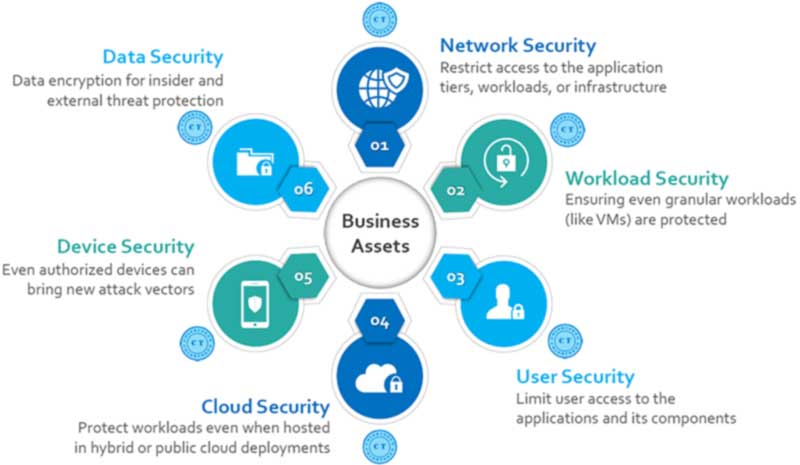
What do we offer?
A complete view of your data centre/cloud service visibility and edge device to end point protection.
- Central management of security. Implement, control and manage threats from one single place.
- Efficient and dynamic mitigation of security threats and attacks. Relieve their network from having to offramp traffic to a central location, and allow for dynamic insertion and removal of security points where and when needed.
- Hardware cost reduction. Specialized vendor appliances are reduced or eliminated.
- Use of existing network appliances Aggregate the legacy functionality via the SDN controller and blend this withother new technologies as they are introduced.
- Dynamic configuration of existing network nodes for the mitigation of an attack. Virtually configuringconnection points, as and when needed, replace often the vendor-specific method of using static pre-configuredpolicies.
- Harmonized view of logical security policies. The policies are propagated across the infrastructure nodesenabling a holistic approach to cybersecurity.
- Visibility of information from one source. Replaces the introduction of network probe elements in differentlocations of the network, which they have to be correlated.
- Integration with sophisticated applications. Use existing information around the network in order to correlateevents to respond more effectively and intelligently to security threats.
- Cost savings and optimisation of services. Get rid of internal firewalls, reduce east-west traffic and reduceaccess while not required dynamically.
- Adaptive learning of the architecture. The platform learns the changes occurring and adapts to provideprotection.
Journey for Achieving Security Policy
Visualise
- Understand business risks in dynamic environment
- Drill down to understand application eco-system
- Analyze traffic in depth to device appropriate policies
Define
- Author policies using Security Policy Templates
- Validate security policies prior to enforcement
- Modularize policies for reusability
Enforce
- Enforce security policies with quantifiable outcomes
- Stay in compliance even with infrastructure changes
Monitor
- Stay up to date when new threats surface
- Understand security effectiveness
- Audit and provide oversight for privileged users
Cyber Analytics
Suraksha SDSec (SSDSec) uses data to fight cybersecurity threats and provides customers with augmented visibility and contextual analytics. Suraksha provides Cyber Analytics solutions based on the best available products (such as ColorTokens), enabling security and risk management teams to make policy decisions with heightened confidence and hunt threats with precision. SSDSec eliminates the need for multiple security products that are expensive, complex to integrate and require the hardware upgrade for full feature use. SSDSec provides a unified platform for your data centre in public or private cloud and is completely infrastructure and vendor agnostic. Through unified threat visibility and analytics, it further integrates with standard threat intelligence feeds and vulnerability scanning tools to make policy recommendation that enhances security and reduces risk posture of the assets in the network infrastructure.
- Visualize traffic across public, private or hybrid environments
- Analyse flow data, build custom reports, with filters and zoom-in at micro-level information
- Discover unnecessary open ports/access points in the network
- Secure critical business applications by validating data flow in application architecture
- Quantify policy recommendations based on a multi-dimensional context of network traffic, vulnerabilities, exposure, and asset value – first in the industry to quantify risk holistically
- Detect threat traversal, resulting in swift incident response and forensics investigations
- Uncover malicious processes taking advantage of whitelist policies
Key Features:
User / Entity behaviour profiling, segmentation and visualisation
High risk user/ entityidentification, visualisation and outlier detection
Machine learning based anomaly detection in internal connections and assigning a risk score
Data exfiltration and anomaly detection in external connections along with graphical representation of why an outlier led to an alert
Advanced threat hunting capabilities an “exhaustive” & “fast” search capability to look for outliers / anomalies
Data Analytics with extended user or entity intelligence covering Logon/Logoff events, AD events, Remote login patterns and network usage
Network Analytics with reporting on network band width usage, connection count, DNS resolutions, to and from traffic from sources of bad reputation
Analyzing exclusive behaviour patterns through machine learning and subsequent reduction false positives over a period of time
Dynamic entity link analysis with User Mapping, detection & highlighting hidden relationships between users, IP addresses, domain demonstration using Network Graph
Reports and visualisation using intuitive analytics dashboards, compounded risk scores and metadata with drill down capability on all reports
What does this mean to you?
- Cost savings and relief from multiple hardware architecture
- Adaptive and flexible, Agentless, Noiseless, Scalable, Self-managing. Risk-aware security
- A measurable metric-based proof of the benefits listed above
- Two case studies, one internal and one for your external customers
- Across the layers of the architecture, private, hybrid and full cloud deployments
Place: Any where in Australia, NZ, Asia, USA and the Middle East
For further inquiries:
Suraksha Pty Ltd
Unit 305, 65 Victor Cr, Narre Warren< Victoria 3805 Australia.

